By Hannah Miller
When it comes to crypto hacks, the story is often the same: Scammers take advantage of a vulnerability in a blockchain’s design and make off with millions, like in the $600 million-plus heist involving the play-to-earn NFT game Axie Infinity and the $77 million theft that took place Saturday on decentralized finance projects Rari Capital and Fei Protocol.

But a $3 million hack last week involving nonfungible tokens from the popular Bored Ape Yacht Club universe exploited a different kind of weakness that isn’t unique to blockchain.
Scammers infiltrated the NFT collection’s official Instagram account and posted a link to a fake website where users connected their crypto wallets for what they thought was an NFT launch. In reality, they had unwittingly opened themselves up to theft. When the actual launch happened on Saturday, users were again targeted when scammers posted links to fake websites that ended up cleaning users out of NFTs worth a collective $6.2 million.
The incidents exemplify a growing trend in which social media is being used as a tool for amplifying and executing crypto and NFT scams. These thefts aren’t just hitting Instagram: Twitter, Facebook, and the chat platforms Discord and Telegram are also fertile ground for these maneuvers, according to Ronghui Gu, chief executive officer of blockchain security firm CertiK.
“We have seen more and more attacks and hacks in web3 and the blockchain industry and many of them have new forms of attack, which we haven’t seen before,” Gu said in an interview.
The escalating social-media cyber threat combines with crypto-based crime hitting an all-time high last year, according to blockchain security firm Chainalysis’ 2022 Crypto Crime Report. Illicit crypto wallets received $14 billion, an 80% increase from 2020. That’s a cost crypto firms and tech giants can’t afford to ignore, and it ratchets up the pressure on them to shore up security and tighten safeguards.
Crypto Copycats
Spam bots and account impersonation are already well-known problems on Twitter. About $2 million was stolen from customers over a seven-month period in 2020 and 2021 through crypto scams advertised by fake Elon Musk accounts, according to the Federal Trade Commission. These tactics are also rife on Crypto Twitter and other platforms upon which crypto users depend.
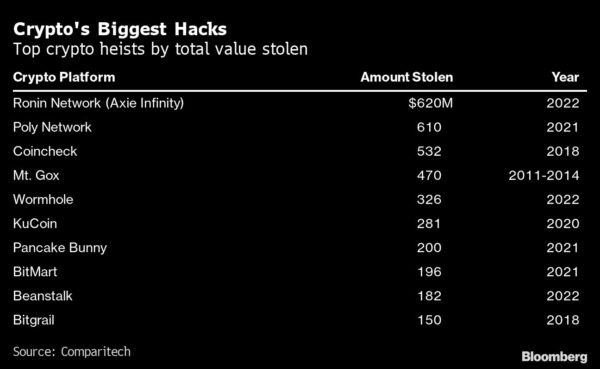
“They heavily rely on this social media to get information about all kinds of different crypto projects like NFTs,” Gu said, adding that he’s even seen fake Telegram accounts that claim to belong to his company, CertiK.
Malicious accounts posing as real crypto companies, projects and entrepreneurs often tout fake giveaways of cryptocurrencies or NFTs. They can also disseminate through spam bots, which are automated social media accounts that can make posts and tag users, just like profiles run by humans. Twitter maintains that less than 5% of profiles are fake or spam, according its first-quarter earnings report — but that doesn’t make them any less of a potential threat.
When Musk announced last week that he was acquiring Twitter Inc. in a $44 billion deal, he said he wanted to improve the social media platform by “enhancing the product with new features, making the algorithms open source to increase trust, defeating the spam bots, and authenticating all humans.”
Identity Theft
It doesn’t have to be a false account disseminating crypto fraud — real accounts belonging to companies can be compromised too. The official BAYC Instagram account used two-factor authentication, according to a statement from Yuga Labs, the developer of the NFT collection. But that didn’t keep the account from being hacked.
The breach of this extra security measure indicates that hackers likely gained access to the account by tricking an administrator through social engineering, according to Gu. This practice involves using personal or professional information to gain someone’s trust, enabling a scammer to then elicit additional data or credentials for a sensitive or valuable account. Both an employee at a social media company and an individual user contacted by a scammer can fall victim to social engineering.
This kind of tactic has been used in hacks of Twitter accounts, with the most notable one being a 2020 incident in which profiles belonging to verified users like then-presidential candidate Joe Biden were used to post a fake Bitcoin giveaway. Twitter employees had been manipulated to provide the access needed for hackers to take over these accounts.
The breach of official crypto accounts has happened on Discord too. Prior to its official launch, NFT marketplace Fractal had its Discord channel infiltrated and used to spread a link to a fake token launch that stole about $150,000 from users.
What to Do?
Crypto scams put more pressure on social media companies to boost security measures and hash out clearer policies on how they plan to better protect users.
When asked about these issues, Twitter, Discord and Telegram told Bloomberg that they all take action to mitigate fraud on their platforms and allow users to report suspicious activity. Meta Platforms Inc., the parent company of Facebook and Instagram, declined to comment on crypto scams on these social media networks and the recent BAYC hack.
Even though cutting out scams is difficult, it’s not impossible, according to Curt Dukes, an executive vice president at the Center for Internet Security, a cybersecurity nonprofit. Requiring users to employ multi-factor authentication to protect their accounts and introducing a patch management system that helps identify and fix security flaws can help decrease vulnerability.
Companies can also provide better education to both employees and users on social engineering and make greater use of tools to verify that a user is human, such as adding a “CAPTCHA” challenge requiring users to solve a puzzle or type in hard-to-read text in order to use the platform.
Musk’s plan to open-source Twitter’s algorithms “definitely gives credibility to the platform,” according to Dukes. Allowing anyone to view Twitter’s code would increase the chances of a security issue being spotted, he said.
As for cleaning out bots, there are machine-learning tools available that could be a big help for social-media companies, but there are tradeoffs invoved, according to Adam Meyers, senior vice president of intelligence at cybersecurity firm Crowdstrike Holdings, Inc. Algorithms can identify posting patterns indicative of a malicious bot account, Meyers said in an interview. Doing so, though, could sharply cut overall user counts, which wouldn’t be ideal for a social-media platform.
“If you’re too good at stopping bots, then that’s going to drive that number down,” Meyers said.
Steps for Startups
Crypto startups can also take concrete steps to improve their security as scams increase, according to Kim Grauer, director of research at Chainalysis. While it’s common for early-stage firms in the sector to prioritize other areas over cybersecurity, “the industry cannot grow so long as it has this kind of ubiquitous hacking happening,” she said in an interview. In addition to hiring security specialists, crypto platforms can also undergo code audits that can help identify potential risks for users, she said.
For some crypto adherents, the ultimate solution lies in web3 — a decentralized, blockchain-based internet that proponents see as a step up from the current state of affiars, where tech companies control the biggest online platforms.
Web3 platforms are owned and managed by users, and developers can build tools that can help with issues like eliminating spam and verifying the identity of users. But a mass migration to a web3 social-media network isn’t realistic for the crypto industry, according to CertiK’s Gu.
Online communities like Crypto Twitter have helped boost mainstream adoption of NFTs and digital currencies. In addition to providing an easy way to promote projects and share information, these social media networks have earned some crypto companies millions of followers.
For crypto startups, walking away from this kind of exposure is too big of a cost. But not taking steps to address security concerns can also take a heavy toll.
More stories like this are available on bloomberg.com.




